Posts
2023
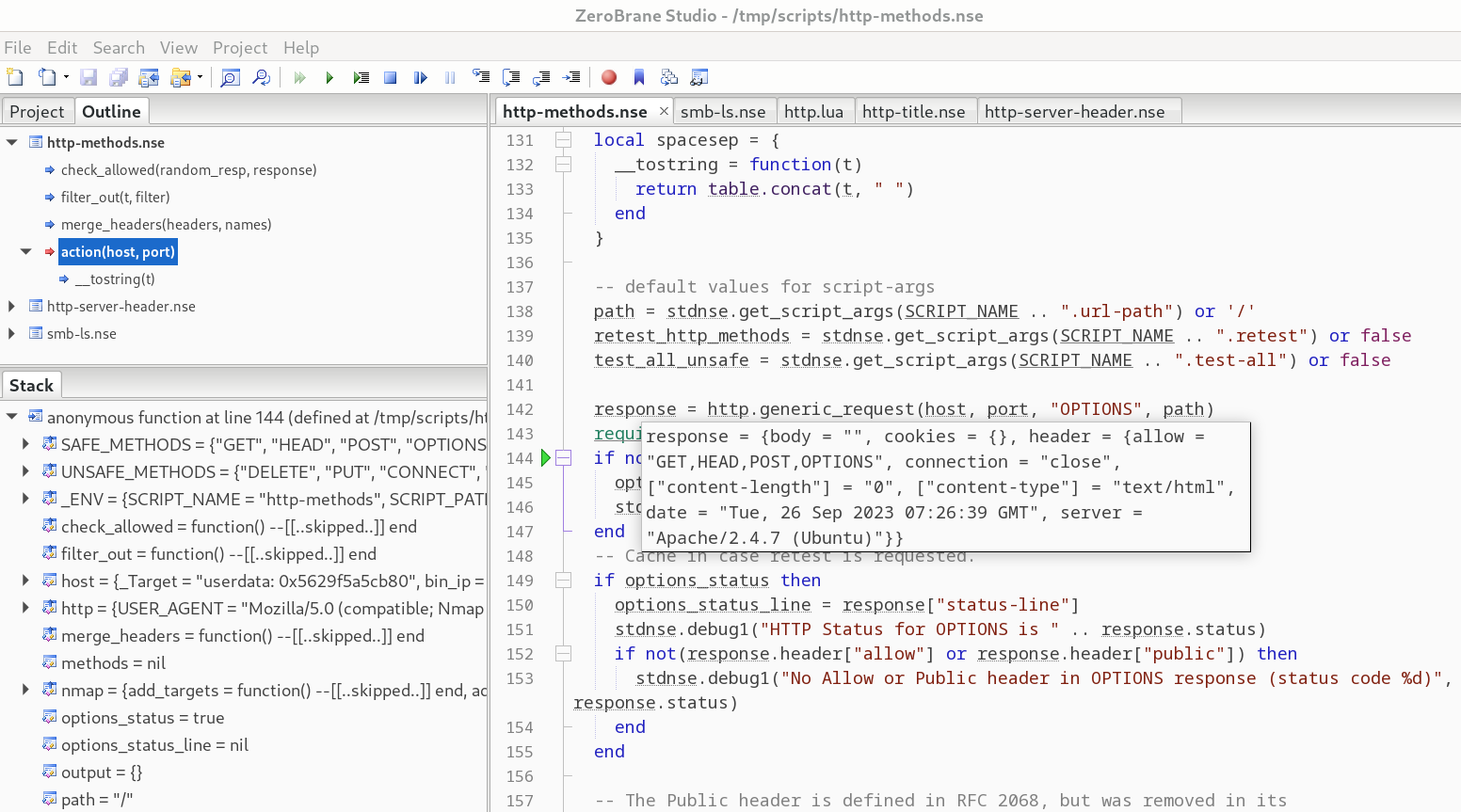
Advanced Nmap NSE Script Debugging
Learn how to debug Nmap NSE scripts like a pro Continue reading Advanced Nmap NSE Script Debugging
2022

Building a Threat Hunting Lab Using Elastic Stack and Vagrant - Part 1
Build a dynamic malware analysis virtual lab with logging to the Elastic Stack / Elastic Cloud Continue reading Building a Threat Hunting Lab Using Elastic Stack and Vagrant - Part 1

Threat Hunting with Elastic
Stack - In-depth Book Review
Threat Hunting with Elastic Stack is a solid book and I’d recommend reading it Continue reading Threat Hunting with Elastic
Stack - In-depth Book Review

Vim, Go and Remote Debugging
Setting up Vim for remotely debugging Go code Continue reading Vim, Go and Remote Debugging
2021
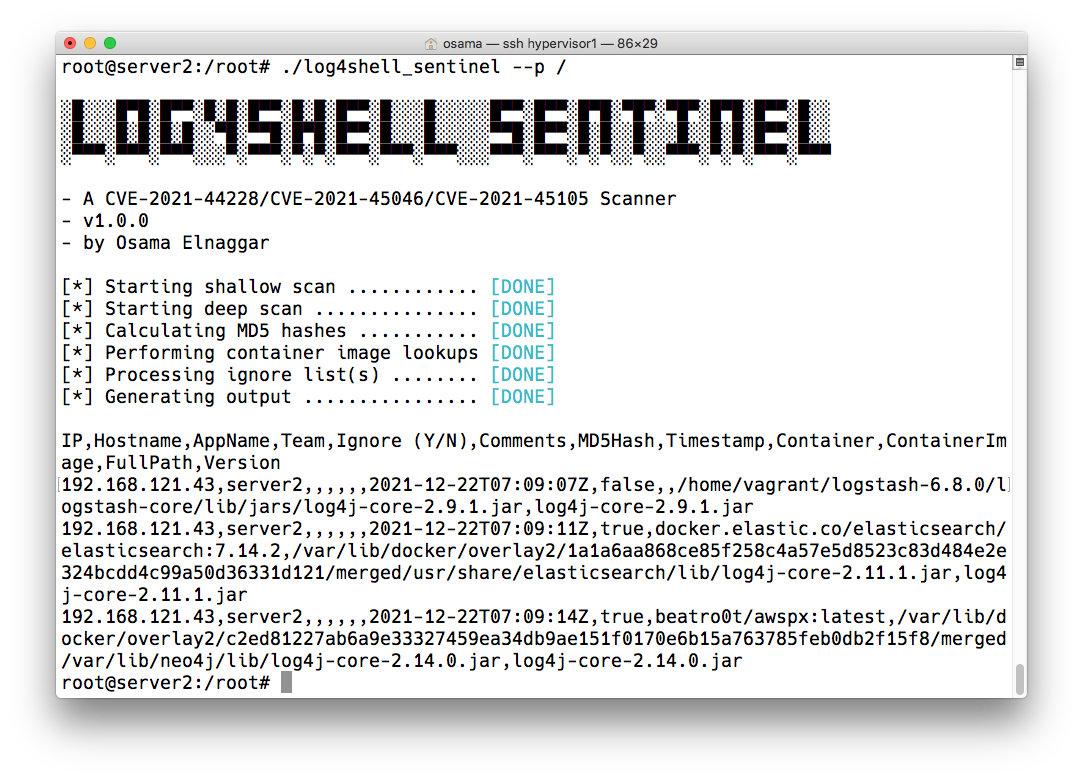
Introducing Log4Shell Sentinel
A smart Log4Shell/Log4j/CVE-2021-44228 scanner Continue reading Introducing Log4Shell Sentinel
Python - Verifying Indirect
Imports At Runtime
Unlike explicit imports that throw an error at application startup, indirect imports in Python throw them when they are actually used. Excessively permissive except clauses can hide them and result in unexpected behavior. Here’s how to verify them at runtime. Continue reading Python - Verifying Indirect
Imports At Runtime

Proxying Application Traffic
Through Tor
A quick look at how to proxy any application’s traffic through the Tor network. Continue reading Proxying Application Traffic
Through Tor

AWS WAF's Dangerous Defaults
AWS WAF’s defaults make bypassing trivial in POST requests, even when you enable the AWS Managed Rules Continue reading AWS WAF's Dangerous Defaults
