Lightning Fast Log Enrichment Using Logstash
on SECURITY, SIEM, LOGSTASH, DPM, ELASTIC STACK
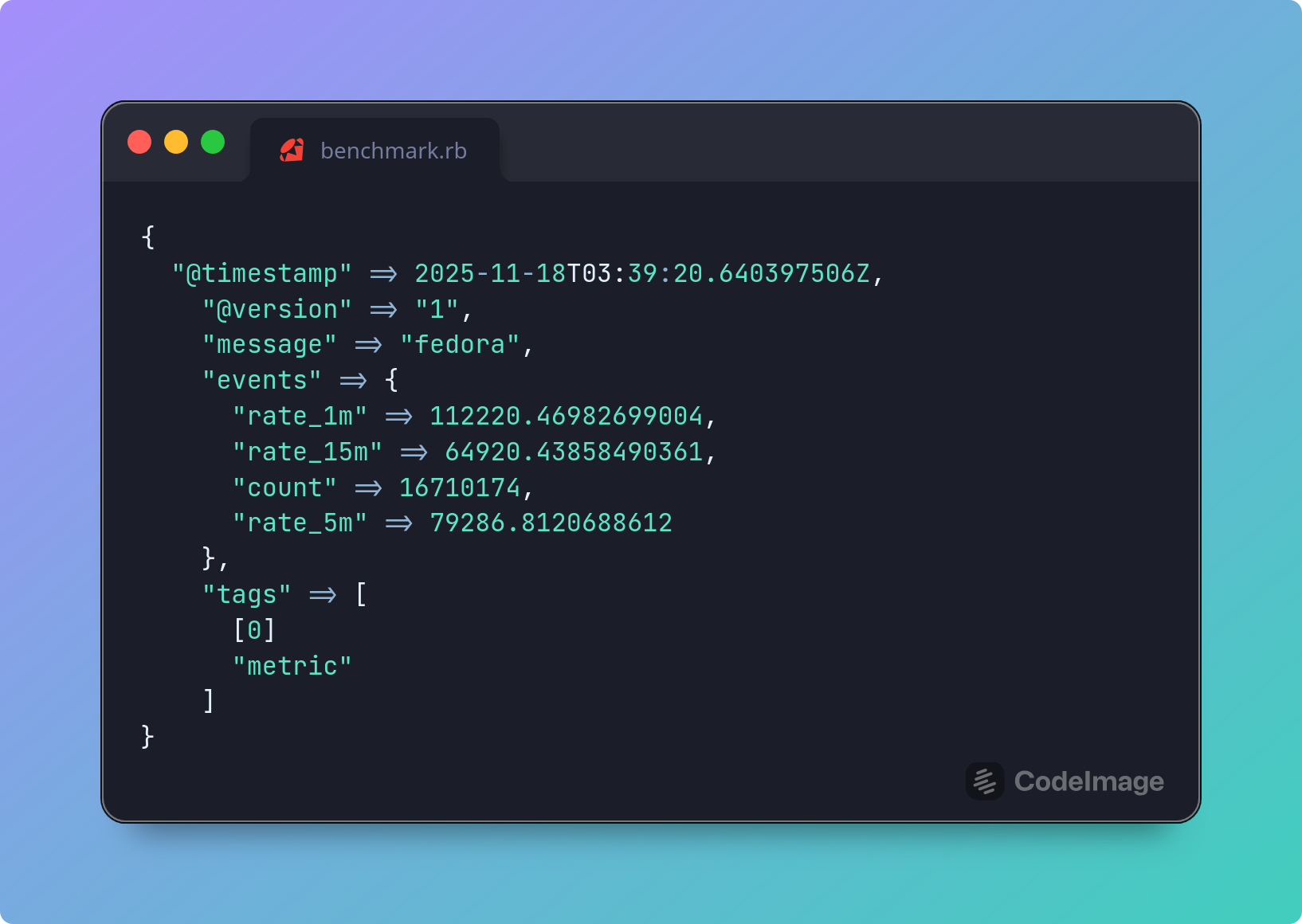
A look at the fastest ways to enrich logs using Logstash

A look at the fastest ways to enrich logs using Logstash
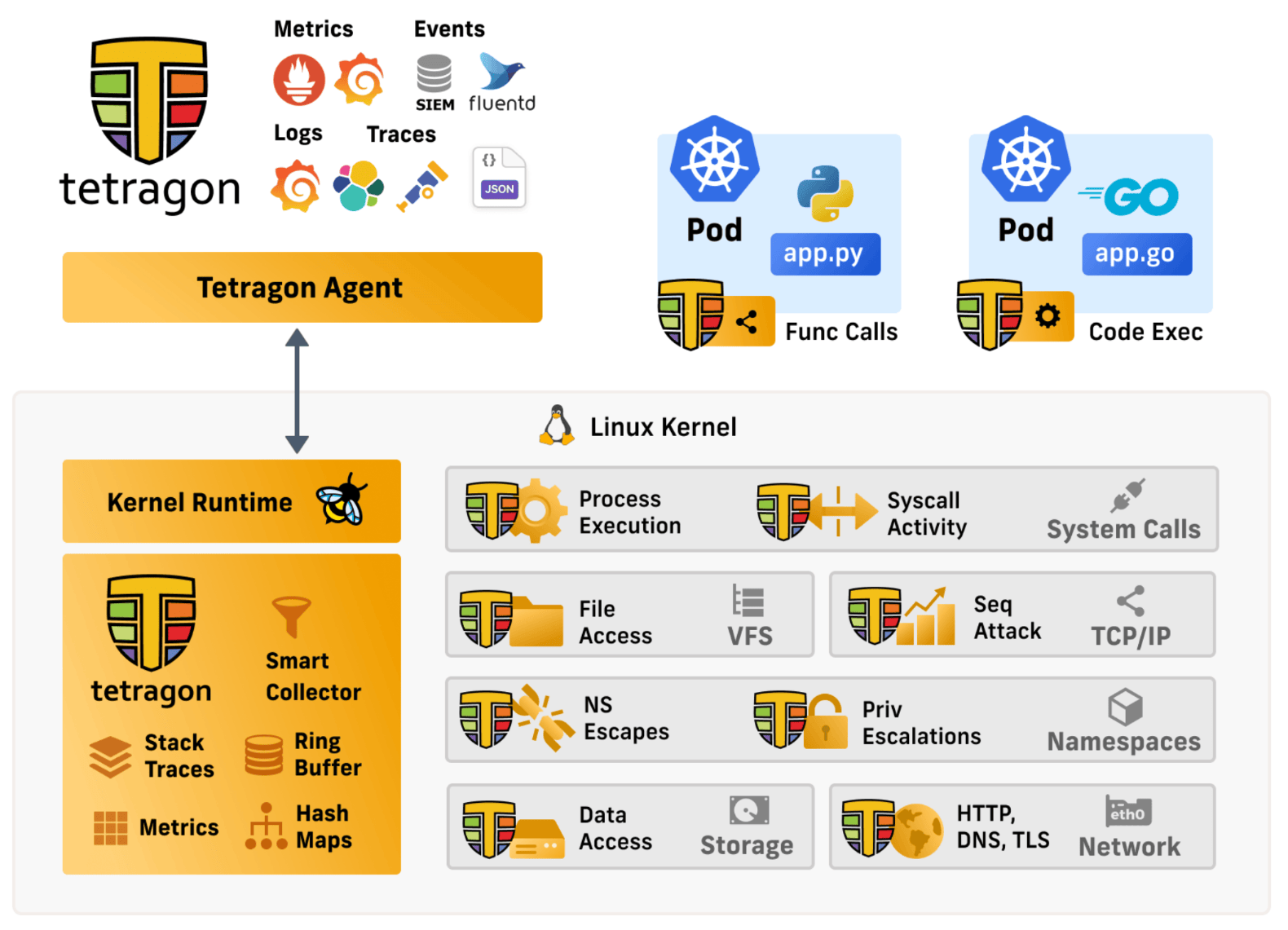
My detailed notes on Tetragon

My in-depth review of Liz Rice’s Container Security, 2nd edition book

Using Bloom Filters to search over a billion password hashes in under a millisecond
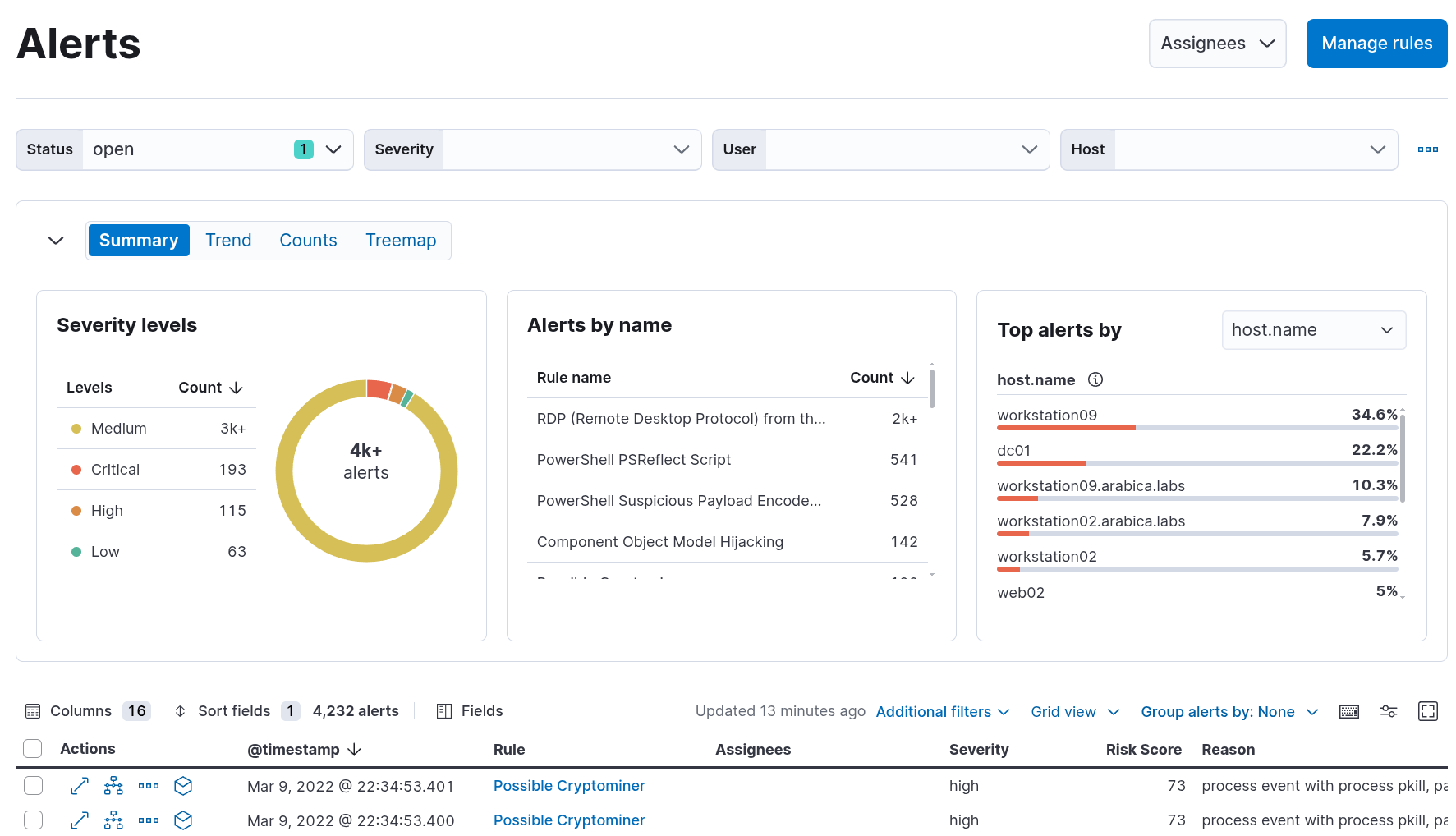
My review of the Elastic Certified SIEM Analyst course

My in-depth review of Liz Rice’s Container Security book
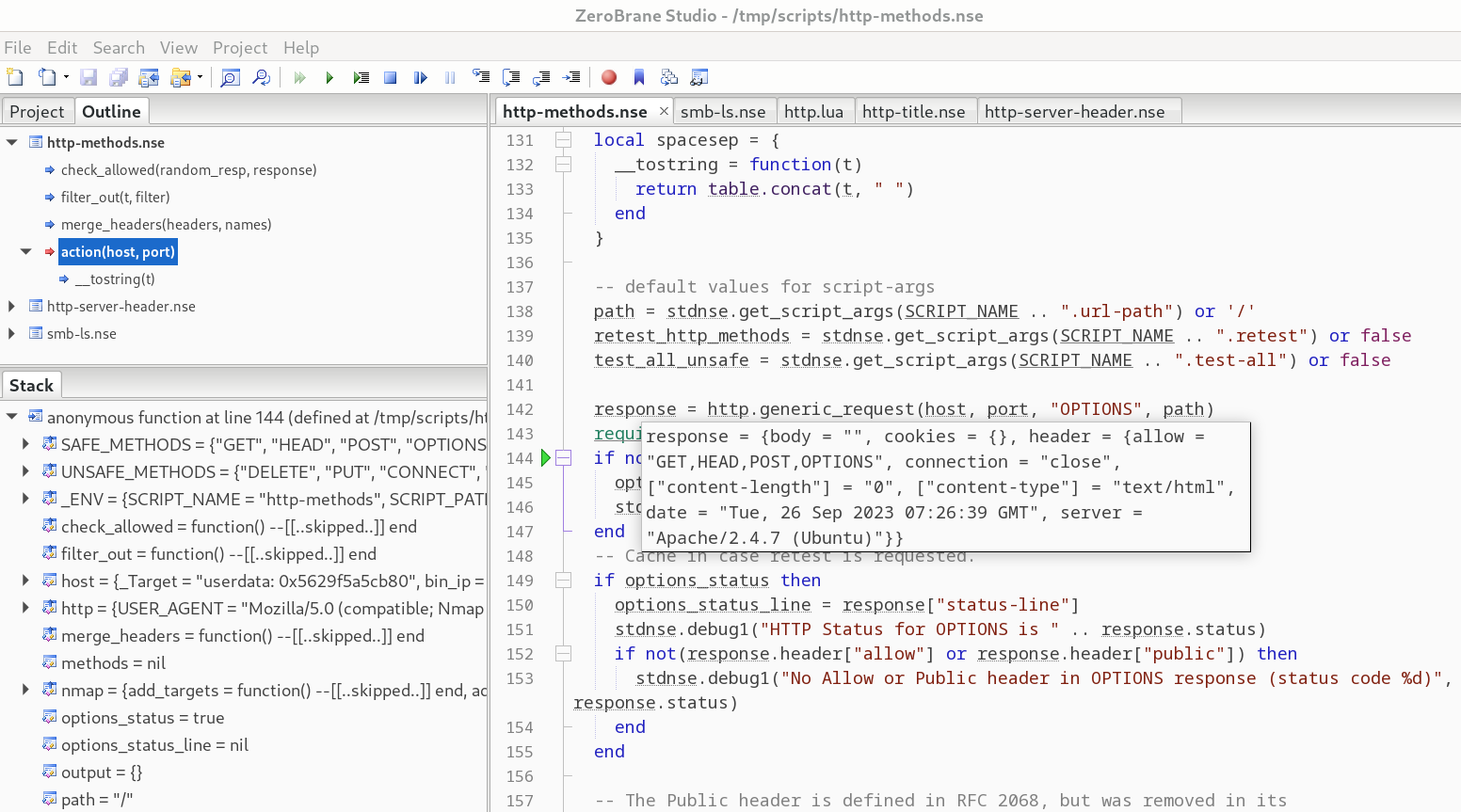
Learn how to debug Nmap NSE scripts like a pro

Build a dynamic malware analysis virtual lab with logging to the Elastic Stack / Elastic Cloud

Threat Hunting with Elastic Stack is a solid book and I’d recommend reading it

Setting up Vim for remotely debugging Go code